How To: Change These Settings Now to Protect Your Data in Case Your Phone Is Stolen

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?Unfortunately, there's always a chance that you or someone you love will have their smartphone stolen. Replacing the phone, although costly, is easy to do — but your precious data is still vulnerable. If a thief is savvy enough, they can access the personal information on a stolen phone and potentially empty your bank account, steal your identity, or worse. Thankfully, we can protect ourselves.Since you can never know when your phone might be stolen, you'll need to take a proactive approach to lock down your data now. By following these tips, you can minimize the chances of a thief accessing your data while increasing the odds of locating your stolen device. Although we live in dangerous times, we do possess strong tools to protect ourselves.Don't Miss: How to Secure Your Texts & Other Communications on Android
Step 1: Install an Anti-Theft AppWith the rise of smartphone theft, many security-focused companies started to expand their efforts from remote threats to those nearby. This led to the creation of several anti-theft programs that combine different technologies to assist users if their device is stolen.Typically, these programs will include remote tracking so that you can locate your device and relay that information to the proper authorities. Remote wiping is another great feature that allows you to wipe the data and prevent unwarranted access. If you conduct regular backups, you won't lose any data, but the thief will not have access.Google provides these two features and the ability the ring your device to help you locate your phone as part of their Find My Device service, which is baked into all modern Android phones. This year, Google combined this program with an antivirus suite to create Play Protect, which acts as a security platform for Android smartphones. If anything happens to your phone, you can use the Find My Device app on another phone (or from the desktop) to see its location on Google Maps. But there's a problem here: Your GPS has to remain on for this feature to work. However, having your GPS always on will drain your battery faster, and it's a security risk in the sense that someone could track you using the same technology. Also, if your phone is turned off, tracking doesn't work.For these reasons, we recommend using Cerberus to supplement Google's default anti-theft measures. This all-in-one anti-theft solution provides all the basic functionality found in Find My Device, but expands on it significantly.Play Store Link: Cerberus (free) With Cerberus, you can remotely turn on GPS so that you can track the device. You can prevent someone from shutting down your device by tricking them with a fake shutdown menu. While they believe they've escaped detection, your phone would really be on and continue its tracking. You can hide the app so that they won't know Cerberus is installed.Cerberus has a web app that allows you to track your phone remotely, and when you first sign up, you'll receive an email with SMS commands that you can use to remotely control your phone. You can remote wipe both the local storage and the SD card. (1) Some of the features found in Cerberus. (2) Cerberus' IFTTT options. But one of the best features is the ability to take a picture or video of the perpetrator without their knowledge. It also has SIM checker that will inform you if the thief changes your SIM card, and it supports IFTTT to set up a series of commands that activate another program based on previous actions. Cerberus also has many more features to assist you if you unfortunately ever have to experience this situation.Cerberus is $5.52 a year, but has a seven-day free trial. We strongly recommend you use this program. By itself, it can be the difference between retrieving your phone or losing everything.

Step 2: Secure Your Lock ScreenOne of the most effective deterrents against unwanted access to your data is a secure lock screen. This starts with enabling one of the authentication methods to enter your device. Do not forgo the lock screen by using just a swipe up gesture or having none. By implementing any authentication, thieves will have some difficulty entering into your phone.As the absolute minimum, we recommend using the fingerprint scanner to enter your device. Fingerprint scanners provide the best balance between security and speed, as most scanners can detect your finger within a fraction of a second. As long as the thief doesn't force you to unlock your device, once they run away with your phone, they won't be able to access any of your data unless they can get your fingerprint. Fingerprint scanners provide adequate lock screen security. However, fingerprint scanners are a flawed security method since consciousness isn't required for access. For example, if you are sleeping on the subway and someone steals your phone, they can use your fingerprint while you sleep to access your phone and turn off the security. That is why, for maximum protection, we recommend a password.A strong password (with over eight characters and a combination of uppercase, lowercase, numbers, and special symbols while having no relation to you or known words) is the best way to impede access, as it requires you to be conscious to implement and is hard to replicate by simple observation. A strong password can last you years without anyone gaining access — although we recommend changing all passwords after 90 days for the best security.
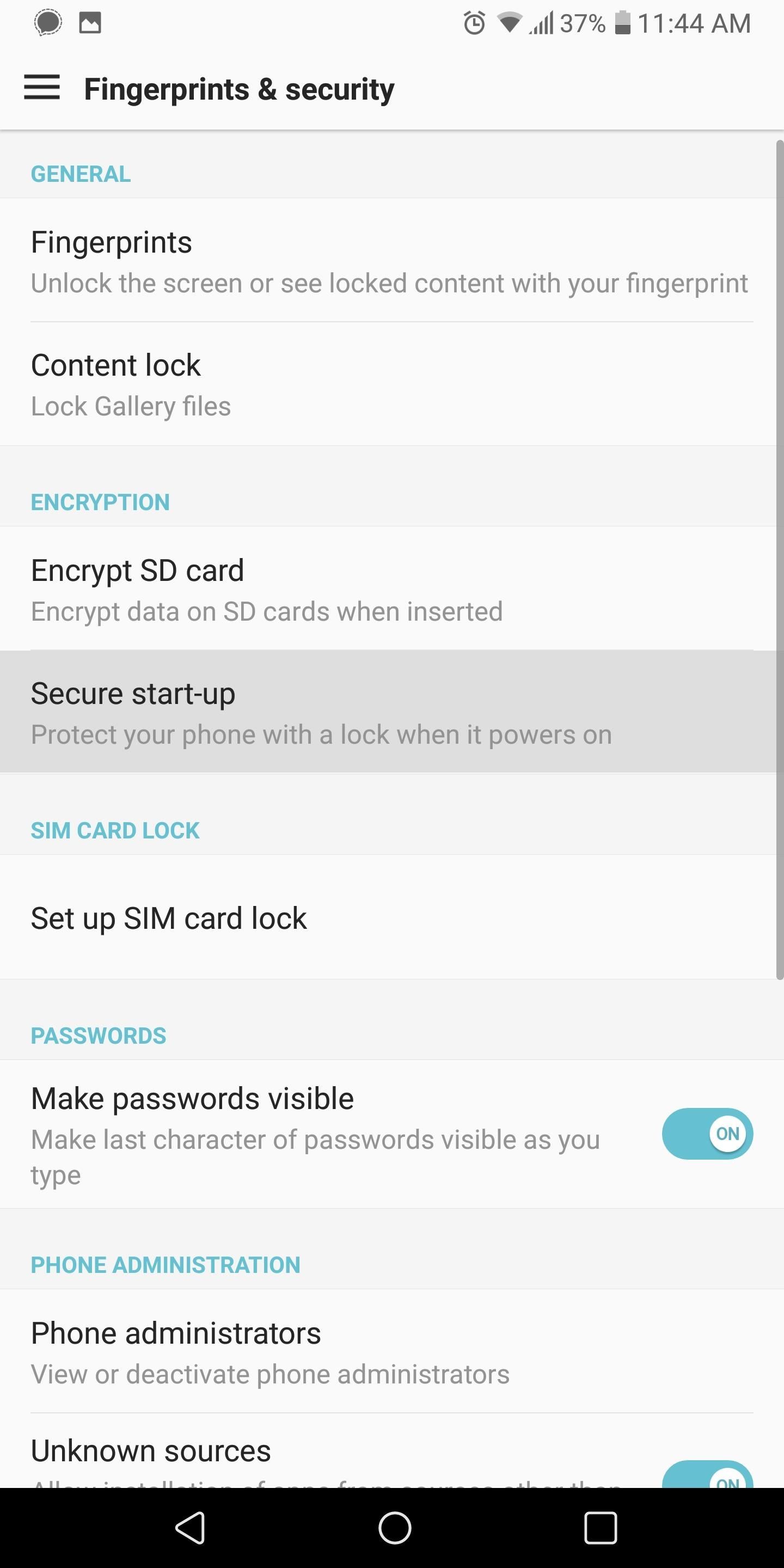
Step 3: Enable Secure Start-UpWith Android 4.4 KitKat, Google introduced full-disk encryption to the platform. What this provided was a virtual safe that locked away all the data stored locally on your device, preventing anyone from accessing it. This encryption was optional, requiring the user to enable it. It prevented access to your phone after it was shut down (or restarted) by requiring the same passcode from your lock screen to decrypt the device for use.Google changed this with Android 7.0 Nougat to a file-based encryption to protect users from themselves. This is because some users would restart their phones and unknowingly be locked out their device for hours, not receiving notifications because the lock screen password hadn't been entered yet. Nougat also removed the default requirement of a passcode each time you restart your device, but you can re-enable it. That way, if a thief turns off your phone to hide his or her location, when they turn it back on, they will not be able to access its data without your passcode.To enable this feature, head to your phone's main Settings menu and select the "Security" option (it might be combined with another feature such as "Fingerprints & Security," depending on the skin). Choose the "Secure start-up" option, then enable the "require X to turn on phone" setting (X representing the lock screen security you are using, whether PIN, password, or pattern). You'll be prompted for this passcode, and then you're done.

Step 4: Secure Your AppsA secure lock screen with secure start-up offers great protection against thieves accessing your data. However, one of the leading principles in cybersecurity is layered security. By having protection at various levels, your data stands a better chance of not being accessed. For an additional layer of protection, we recommend securing apps individually.Not all apps contain precious data that could compromise us if accessed by another individual. However, for the apps that do, you can use an app called AppLock to provide additional protection.Play Store Link: AppLock (free) With AppLock, you can secure individual apps from being accessed without proper authentication. AppLock allows you to use either a pattern, PIN, or fingerprint to secure individual applications.AppLock also can prevent certain actions from being conducted without a passcode, such as installing or uninstalling apps, receiving calls, or toggling connectivity radios. It allows you to schedule protection based on the time of day or location if you choose.
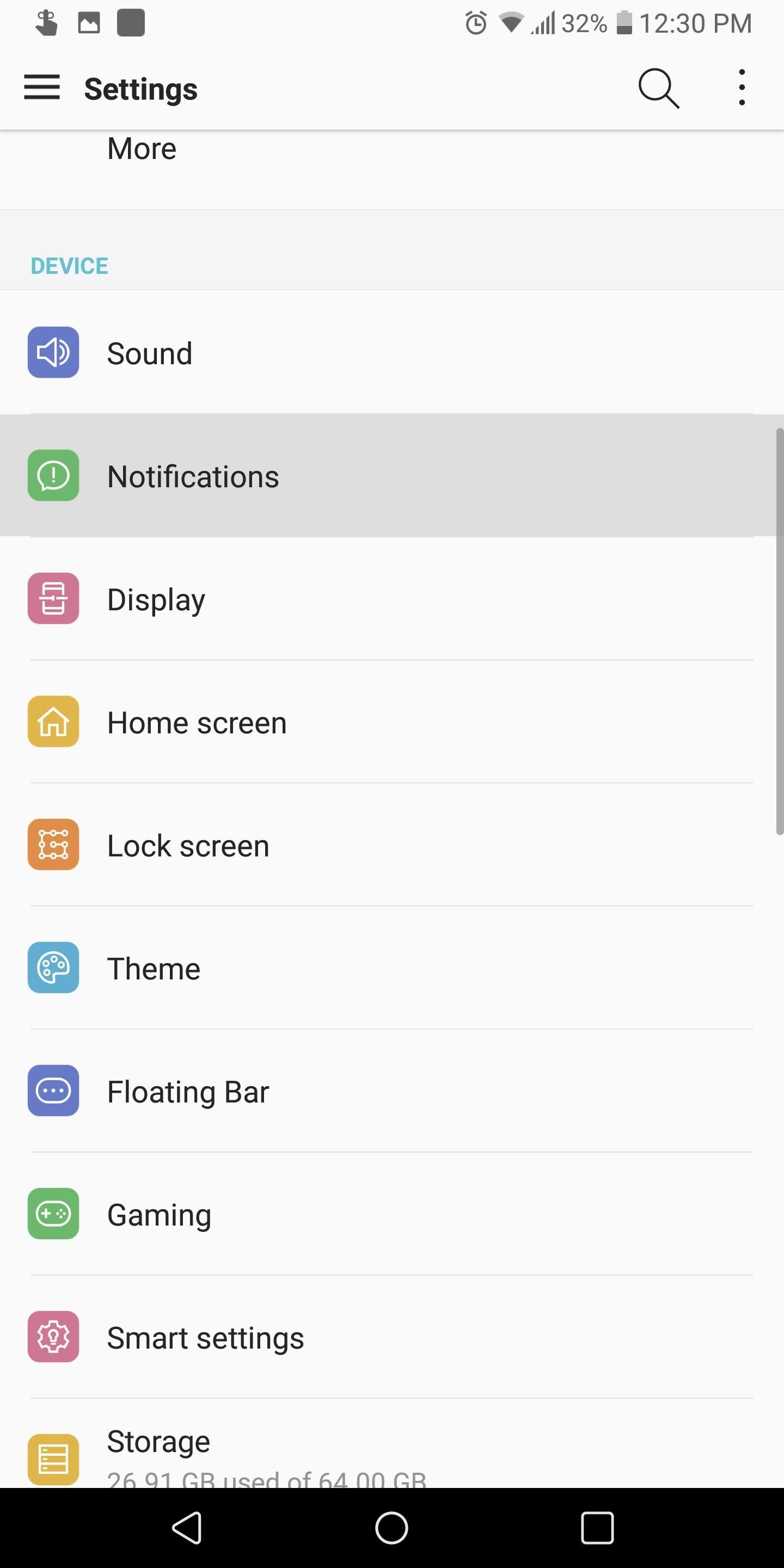
Step 5: Hide Info from the Lock ScreenEven without requiring proper authentication, the notifications presented on your lock screen can contain valuable data. Although convenient, notifications such as text messages can be read from the lock screen without ever needing a passcode.To disable this, head to the Settings menu and select "Notifications" (for some skins, you'll need to search for "notifications" instead). Select the "Lock screen" option and choose "Hide sensitive only." Once enabled, the lock screen will still show all new notifications, but it will block the contents of messages, preventing someone from reading them without unlocking the device.
Step 6: Use a Password ManagerIt is convenient to use our favorite apps without having re-login in each time. Yet, if they are unlocked for you, they would be unlocked for a thief if he or she was able to gain access to your device. Hence, always log out of all important apps, such as banking or e-commerce. This way, your data is protected with layered security. Also, if possible, don't autofill your user name, as this can be used to retrieve your password. Hackers have used usernames to call up customer support to gain the access to accounts.To take things a step further, use a password manager to create secure passwords for all your accounts. If you try to make up a secure password for all of your accounts, you'll likely forget them — especially if they follow the good password guidelines.Password managers, such as LastPass, assist with this by only requiring you to know one strong password. LastPass can generate passwords for all your other accounts and store them in an encrypted database. The password generated can be as complex and long as necessary since you are not required to remember it.Play Store Link: LastPass (free) There may be more smartphones stolen each year, but the tools available now allow you to better protect your data and minimize the damage. By using these recommendations, you can safeguard your smartphone's data in the event it ever falls into the hands of a thief.This article was produced during Gadget Hacks' special coverage on smartphone privacy and security. Check out the whole Privacy and Security series.Don't Miss: Android Security 101 — How to Browse the Web SafelyFollow Gadget Hacks on Pinterest, Reddit, Twitter, YouTube, and Flipboard Sign up for Gadget Hacks' daily newsletter or weekly Android and iOS updates Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover image and screenshots by Jon Knight/Gadget Hacks
Using a HDTV (High-Definition Television) antenna, based on the DB4 design, is 1 of the most effective ways to retrieve HDTV signals. Purchasing this type of antenna at a store will cost you at least $40. However, you can build such an antenna yourself at a much lower cost. The following is a guide on how to make a HDTV antenna.
Powerful Modern Homemade HDTV Antenna
This video will teach you guys how to increase your download speed, lower lag, lower ping and reduce buffering on your internet by using a few of my best methods, this is intended for ALL users
How to Speed Up Downloads when Using Internet Download
So you need to charge it. By using a charging dock like this one, you can use it throughout the night as a nightstand clock, providing you with an alarm clock, display alerts and the current time. Right now, you can get this 38mm/42mm Apple Watch charging stand (plus charger) for just over $21.
How to charge an Apple Watch, and how long it takes to fully
How To: Trigger traffic lights to change from red to green How To: Make traffic lights change w/secret code (FAUX-TO?) How To: Make a motion triggered spy camera How To: Shut off your alarm clock with a light phaser How To: Hack a transistor radio to hear Air Traffic Control
How to Trigger Green Traffic Lights - stepbystep.com
The Google Maps Android API allows you to include maps and customized mapping information in your app. Key developer features Add maps to your app. With Google Maps Android API v2, you can embed maps into an activity as a fragment with a simple XML snippet.
Find Your Location History in Google Maps or iPhone
Yesterday, Apple announced the iPhone XS, iPhone XS Max and iPhone XR. These three new iPhones for 2018 officially replace the iPhone X, which Apple pulled from its store after the announcement
iPhone XS Vs iPhone XS Max: What's The Difference?
How to Use Your New Terabyte of Free Flickr Storage for More
The Best Buy Mobile team explains how simple it is to send a text message on your Android enabled cell phone. With the Android platform on a large amount of mobile phones today, chances are you have one.
Text message error code Dst.Rs.Sht. (35) on Palm Treo
Google Play Music offers an unlimited music streaming subscription paired with YouTube Red, but it's more than that. Even if the music you want to listen to isn't available in Google's streaming library, you can add it to your own personal Google Play Music library and listen from any device.
My songs won't upload to Google Play Music - Google Play
Today, we are going to help you, to unlock the bootloader, Install TWRP, and Root Nextbit Robin. Nextbit is a new Android device manufacturer in the market, which is believed to bring uniqueness to the platform. Nextbit's first and latest piece of goodness - Robin, is all about storage and space. The phone is designed to never run out of
Nextbit Robin phone will be no more as new owner Razer - CNET
How To: Get the Galaxy S5's New S Voice App on Your Samsung Galaxy S4 Telegram 101: How to Password-Protect Your Chats for Extra Security How To: Get a Feature-Packed, iPhone-Like Lock Screen for Your Galaxy S6 or Other Android Device
Lollipop's 'On-Body Detection' Smart Lock Keeps Your Android
If your calculator app has disappeared from your iPhone (and the Control Center on your iPhone), don't panic. Beginning with iOS 10, Apple gave users the option to remove Apple stock apps from our Home screens. When the feature first became available, I started deleting every Apple stock app that I didn't use.
Easiest Way To Fix A Stuck Or Dead Pixel On Your iPhone Or
I know it's what comes built in on not-quite-new Android, but it's also an outdated and notoriously troublesome class. Today we have so much better in java.time, the modern Java date and time API, and its DateTimeFormatter. Yes, you can use on lower API level Android too when you add ThreeTenABP to your Android programming project.
set date format dd.mm.yyyy in Android v5.1. despite GUI
How do I unfriend or remove a friend? | Facebook Help Center