How To: Lock Down Bluetooth, Force HTTPS & Adjust Other Options to Secure Your Android Device
Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.Based on surveys conducted by the Pew Research Center in November 2016, an impressive 77% of US adults own smartphones. Beyond the States, it's assumed that somewhere close to two billion people use these devices across the world, and about 88% of them are Android-based.Not all of these Android users are aware of certain features on their smartphone that are commonly exploited by malicious persons for financial gain or to scrape sensitive information. With an ever-growing pool of people constantly connected to the internet, the number of potential unscrupulous persons increases—and you don't want to be one of the suckers they take advantage of, do you?
Basic Security Principles for All TechnologyBefore we look at ways to secure an Android, a few others points must be considered to ensure the most secure setup. Not only is securing your phone a critical operation, ensuring that the accounts you use follow a solid security protocol is important as well.1. Don't Leave Your Devices UnattendedIt should go without saying, but whenever you are in public, a shiny piece of technology sitting unattended is asking for trouble. Admittedly, I'm personally guilty of this since most of my work is done outside my home, so there are times I step outside to take a call and leave my computer unattended. However, I make sure to lock my computer and ensure that any handheld devices are always either tucked away out of sight, or within arm's reach.2. Use Unique, Strong PasswordsSure, it's much easier to use the same password for everything, but this kind of laziness makes it quite simple for someone to access all your accounts by knowing a single password. Generate unique passwords for every account you create by using a combination of uppercase and lowercase letters, numbers, and symbols (if allowed). If you've ever wondered the strength of your password, there are sites that let you check it.Don't Miss: Advice from a Real Hacker: How to Create Stronger Passwords Dashlane's tool will show you just how good or bad your password is. 3. Update Your SoftwareSoftware is regularly updated for a variety of reasons, including the addition of new features, bug fixes, and most importantly, security patches. Think of your devices like a pirate ship; As time progresses, the vessel ages and wears. Holes develop which need to be plugged, or it will take on water and sink if not addressed.Sometimes, we tend to hold off on installing major updates, as it is common to hear horror stories of OS overhauls causing major issues. This holds true for apps as well, but such issues tend to be resolved much quicker. Also, some Android devices inherently feature the ability to uninstall updates in the app manager found in your settings, and it's possible to backtrack with other methods such as using Pyler's AppDowngrader, though the device needs to be rooted.
Enhance Security on Your Android with These 6 TipsNow that the basic principles of security are out of the way, let's get into the lesser known tips.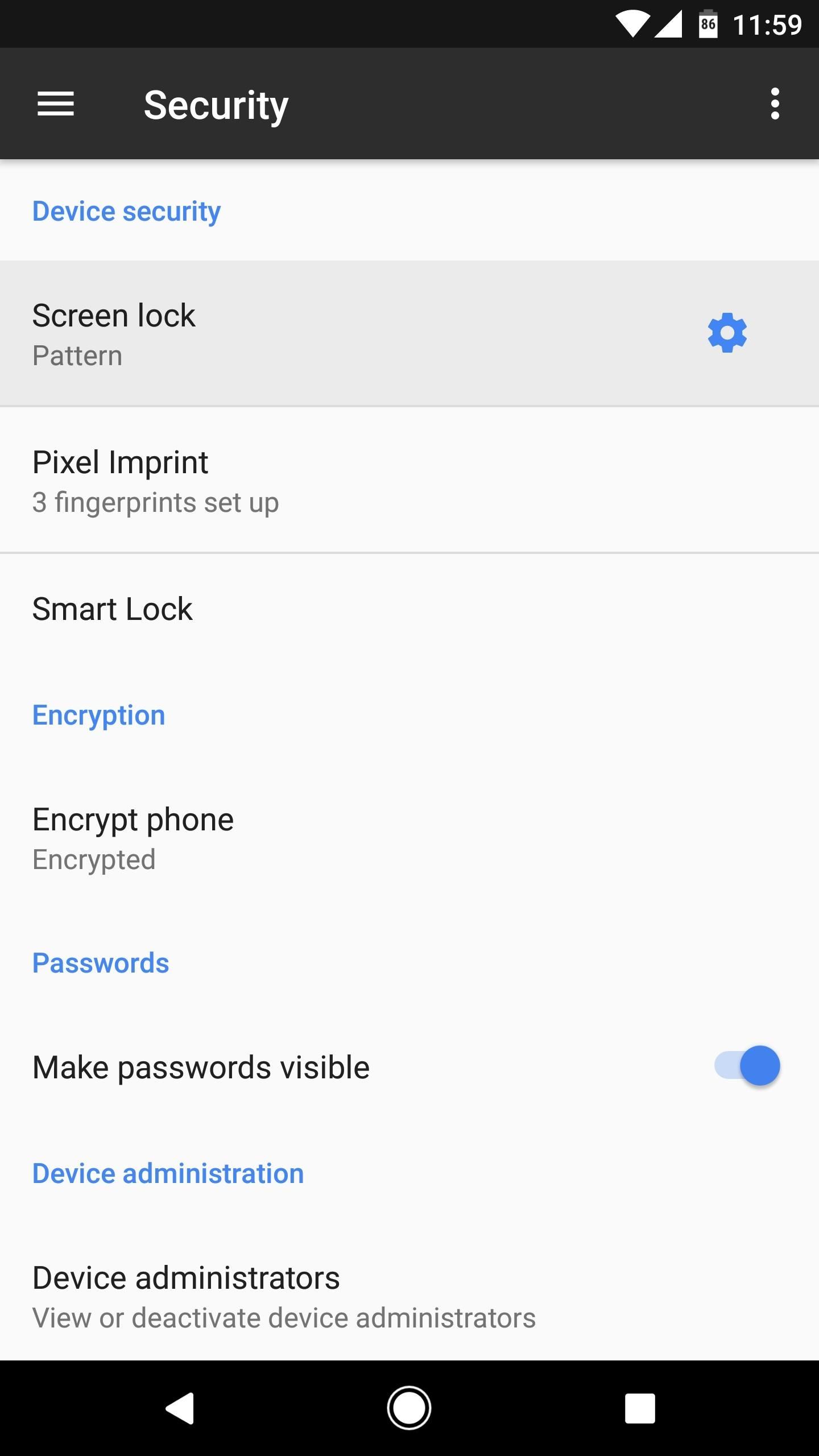
Tip 1: Use the Screen Lock & Modify SettingsUsing a secure lock screen (pattern, PIN, or password) prevents nearby people from snooping through your phone. It also prevents interfacing with a computer, as this device needs to be unlocked in order for a PC or Mac to read its contents.Generally, this feature is found under the Security link within Settings. As seen below, I have a pattern set up, as this method (or a PIN) are the most secure ways to lock a device, since other locking methods, such as facial recognition, can be spoofed. Further, by setting the Lock phone after (or Automatically lock) option to "Immediately," it virtually removes the possibility of anyone looking through a device after turning off the screen. Another good practice is to keep your phone hidden while drawing your pattern or typing in a PIN. Starting with Android 5.0 Lollipop, there's a new feature called Smart Lock that allows the device to remain unlocked when certain conditions are met, as seen in the following pictures. Use caution if you have this setting enabled, and consider your environment when adding "Trusted places." Ideally, avoid using the "Trusted devices" setting altogether, as this will keep your phone unlocked at all times while it's connected to a Bluetooth accessory.
Tip 2: Encrypt the DeviceEncryption is highly useful tool for protecting your information in the event a device is ever stolen. Though a screen lock is useful for preventing unwanted access, most devices offer a built-in utility to apply AES 128-bit encryption that prevents all but the most skilled individuals from accessing files on the phone.Virtually every Android offers this option, which is labeled "Encrypt device," and can be found under the Security link within Settings. The only problem with encryption is it marginally slows down read and write speeds, but it shouldn't have a noticeable effect on performance.
Tip 3: Use Android Device ManagerEver plug your phone in when you're away from home, leave in a hurry, then find yourself in a panic? It's stressful, but as long as the device is powered on, location services are enabled, and you're logged into Google, the phone can be located.By using Android Device Manager, you can pull up the phone's location, which is highly useful when you can't remember where the device was left. Further, if it appears in a strange location (possibly indicating it was stolen) you can remotely wipe the data on the phone.Don't Miss: Use Android Device Manager to Find, Wipe & Lock Your Android Phone or Tablet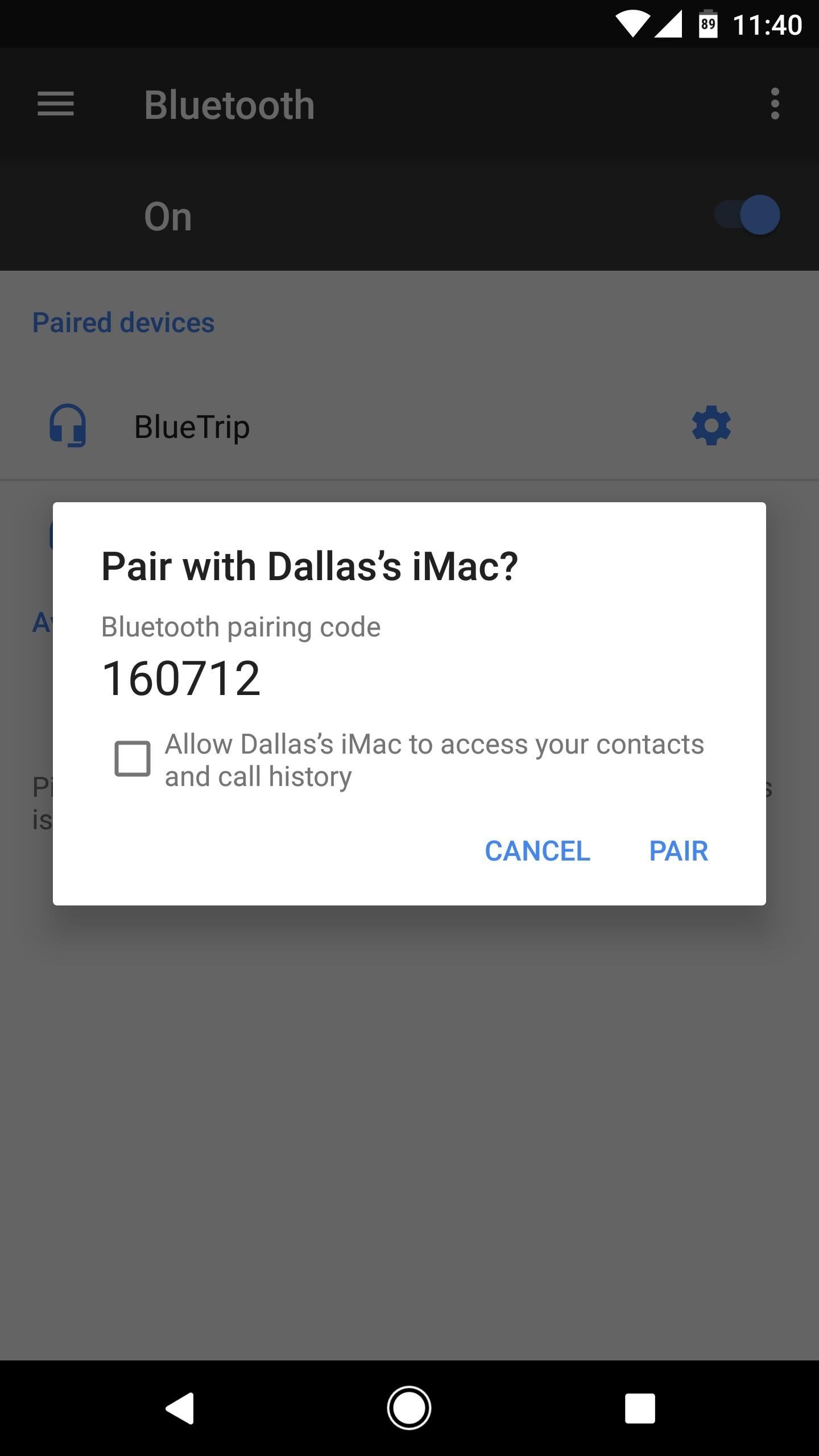
Tip 4: Lock Down BluetoothAs convenient as Bluetooth may be for connecting to devices such as stereo systems, headsets, and other peripherals, it's a two-way street that opens a door for nearby attacks known as Bluejacking or Bluesnarfing. Essentially, whenever Bluetooth is activated, there's always some degree of risk, so the safest option is to turn off this feature when not in use (this helps save some battery life as well). The process of pairing Bluetooth devices isn't the most secure. Early incarnations of Bluetooth were incredibly insecure, but current versions implement encryption based on the SAFER+ algorithm. Even though the connection is encrypted, paying attention to your devices while in use can help prevent unauthorized connections in cases where you could inadvertently enter a passkey should an unknown device attempt to connect.We recommend removing paired accessories after use, as this is the easiest way for someone to gain access without a brute-force attack. In some cases, changing an accessory's name to something currently paired to one of your devices is all it takes to gain access.
Tip 5: Force HTTPS for Sites You Regularly VisitMore than likely, you use Google Chrome on your Android, although many other options exist. With Chrome, you can add domains into the browser setting such that you will always connect using HTTPS.Open up Chrome and type chrome://net-internals/ into the address bar, then navigate to the HSTS link. Add the URL for your favorite sites in the Domain field, then tap the "Add" button when finished. This will ensure sites will connect using an SSL certificate, which is considerably more secure. The catch is, sites without an SSL certificate will not open, so it would be best to avoid adding sites where you don't login.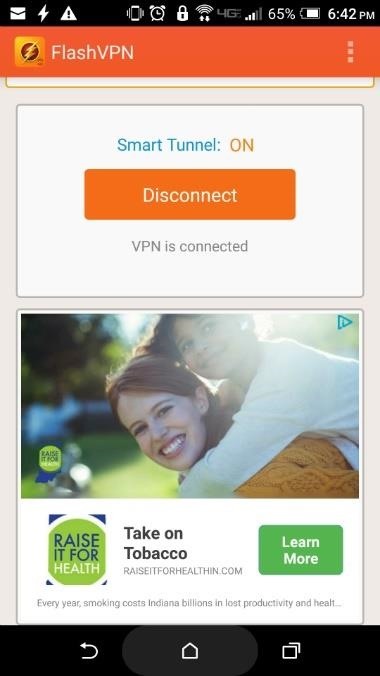
Tip 6: Use a VPN When PossibleA virtual private network, or VPN, works by filtering your internet traffic through a secure, usually encrypted server. If you use your phone for work in a situation where you connect to a company server, you may already have something similar implemented, as business systems generally sit behind a firewall. Most devices have a built-in, generic VPN client, but some setups, such as networks behind a Cisco ASA, require proprietary software to properly interface.Aside from business purposes, it's a good idea use a VPN for everyday use, especially if you use open Wi-Fi access points in a public place. There are plenty of VPN applications available on Google Play, but most require a monthly payment. Two good, (mostly) free options include FlashVPN, which is free but ad-based, and TunnelBear VPN, which doesn't charge for the first 500 MB each month, but will charge for unlimited use. Setting up FlashVPN (left) or TunnelBear (right) is as easy as installing the app, then tapping "OK" when prompted to enable the VPN. Other measures are available for boosting the security level of an Android device, but if you followed the tips above, you're likely in pretty good shape. Then again, extra security never hurts, so make sure to check out the article linked below for more ways to stay secure.Don't Miss: 10 More Ways to Lock Down Your Android DeviceFollow Gadget Hacks on Facebook, Twitter, Google+, and YouTube Follow Android Hacks on Facebook, Twitter, and Pinterest Follow WonderHowTo on Facebook, Twitter, Pinterest, and Google+
Cover image by Dallas Thomas/Gadget HacksScreenshots by Nick Epson/Gadget Hacks
Again, most of these are basic things that just may not be obvious to new and old users alike, but they are definitely good to know about, along with the other cool HTC One M8 features we've shown off (lock screen gestures, new themes, a camera shortcut, more Quick Settings customizations, and font styles) and the ever so important battery
HTC One Gadget Hacks - m.youtube.com
Star Trek The Original Series A 1960's sci-fi action adventure series set in the 23rd century based around the crew of the USS Enterprise, representing the United Federation of Planets (including earth) on a five-year mission in outer space to explore new worlds, seek new life and new civilizations, and to boldly go where no one has gone before.
Watch Star Trek - Original Series Episodes Online | SideReel
For instance, a developer who wanted to learn how to program cell phones might use an Android development board to understand that operating system. Some developers need to build boards of their own to share with others; in these cases, a development board kit might be helpful.
How To Create And Program USB Devices | Electronic Design
It's easy to send animated GIFs from your iPhone using the Messages app, using the built-in app drawer added in iOS 11. In this tutorial we show how to make use of this feature, and amuse and
How to Download & Save GIFs on iPhone (UPDATED FOR 2018
This video tutorial program is designed to promote ground crew safety when working under and around helicopters during external load operations. This is not a safety-training and is only intended to be used with the participation of a ground crew safety officer, trainer or other qualified personnel.
Pimp Your Copter - Metacafe - Online Video Entertainment
Note that Spirit is a jailbreak for every device. It will NOT unlock your iPhone. How to jailbreak your iPhone, iPod Touch, or iPad with Spirit. Step 1: Download Spirit from our download page. Step 2: Make sure you have at least version 9 of iTunes. Step 3: Back up your iPhone, iTouch or iPad in iTunes, just in case something goes wrong.
How To: Jailbreak Any iPhone, iPod Touch or iPad
Or you can download youtube video using youtube app and watch them later without any internet connection. Lengthily 720 pixel high quality video always buffer even in high speed connection. In such condition you can't see 1 hour video in a day.
Apple TV: Worth it without Internet connection? - iPhone
Oct 04, 2016 · Surge pricing isn't arbitrary. It happens during times when -- and in locations where -- drivers are in high demand. Here are nine ways to get around surge prices and avoid having to turn to Kickstarter after accidentally spending your rent money on a $360 ride
Is your friend getting a cheaper Uber fare than you are?
Asus ZenFone 6 was launched in Spain last week, and now the Taiwanese computing giant is getting to ready to release the phone in India. The phone has been listed on e-retailer Flipkart.
Asus Zenfone 5Z (Z5620KL) Price in India, Full Specs
Through the App Store, iTunes Store, and Apple Books, you can gift apps, music, movies, TV shows, books, audiobooks, or money as Apple ID credit. If you find an item in the App Store, iTunes Store, or Apple Books that you want to send to a friend or family member, you can gift it to them.
Movies, music, books and games: Apps to track your media · Exist
A Note About Tasks & Profiles. To automate events with Tasker, you'll need to create a profile and a task. You can do this in any order, but you may find it helpful to create the task first, because the task is what your phone will actually do when the automation scenario kicks in.
How to Totally Automate Android with Tasker Profiles | Beebom
0 comments:
Post a Comment