Android Security 101: How to Secure Your Communications & Messages
Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.Securing your messages requires addressing three components of communication: The network, the apps, and your social decisions. By implementing our recommendations, you can make it significantly harder for someone to access your messages. These steps are not foolproof, but they'll make it less likely that you are a victim of the next major cyber attack.Don't Miss: The 4 Best Phones for Privacy & Security
Step 1: Get a VPNWhen it comes to securing your communications, you'll first want to focus on the travel of data. VPNs, or Virtual Private Networks, provide security and privacy for your data by encrypting all traffic. Encryption is like a virtual safe that hides your data from malicious individuals. By using encryption, your data (including its contents) is protected.VPNs also provide privacy by hiding your IP address. Your IP address is like your home address, identifying your smartphone to the internet. Your network uses this information to send and receive data to and from your device, but if this information falls into the wrong hands, hackers can conduct cyber attacks. VPNs hide your IP address by moving all your traffic through their servers before moving to its destination and changing the source IP address. By doing so, your real IP address remains hidden from the web.There are many excellent VPN services on the Play Store, but our recommendation is NordVPN, as it provides a balance of security and speed. NordVPN uses the highest encryption method to protect your data and has over 1,000 servers in 61 countries, allowing it to maintain a fast data connection while doing so.Install NordVPN for free from the Play Store Its Android app is very simple and straightforward. Once you open the app and log into your account, while on the main page, select "Quick connect." A pop-up will emerge asking if you wish for NordVPN to control OpenVPN for Android. Select the checkbox asking if you trust the application then, choose "OK."Afterwards, another pop-up will emerge asking if you give NordVPN permission to intercept all network traffic. Choose "OK" and now NordVPN will connect to the nearest server that has the lowest traffic ensuring minimal lost of internet speed while using VPN protection. NordVPN also has a feature known as CyberSec, which provides additional protection by actively monitoring the websites you visit to protect against malware, ads, and botnets (attacks which use your smartphone to attack other devices).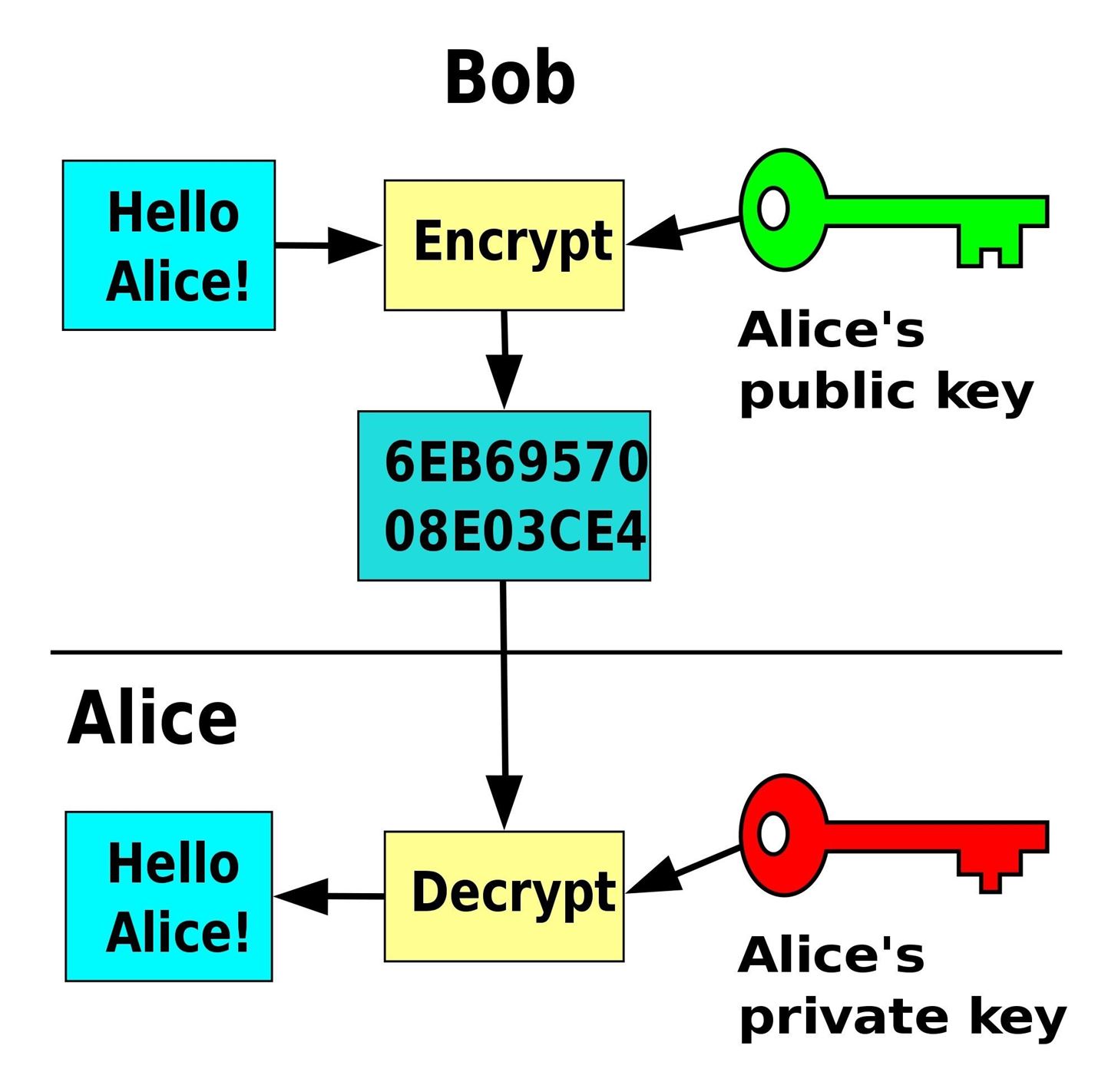
Step 2: Encrypt Your Phone Calls and MessagesBesides a VPN, the applications used for communications should also provide some level of encryption. If the app is the weak link in our security fence, our communications can still be compromised by an external threat.Recently, the news has talked about end-to-end encryption and how many popular messaging apps are using it to protect their customers. End-to-end encryption is when an application encrypts your data both on each device and during travel, providing complete protection.For example, if Bob wishes to communicate with Alice, both Bob and Alice would generate a pair of keys — one public key, and one private key. Before communication begins, Bob and Alice must exchange their public keys. Their smartphones exchange their keys using a temporary secret code known by both parties or other secure protocols that ensure the safe passage of the keys.Once exchanged, Bob can compose his message and encrypt it using Alice's public key. Only Alice's private key can then decrypt the message. As long as Alice's private key is uncompromised, the message can only be read by Alice. When Alice replies back, she will use Bob's public key to encrypt the message, and just Bob's private key can decrypt it. Image by Winstonlee/Wikimedia Commons However, with regular messages, your service provider is the weak link, as many cell carriers collect data about you and your communication for advertisement purposes. Typically, no keys are generated, and instead, your device is sending the message hoping that it arrives unaltered or viewed. You can achieve end-to-end encryption by using instant messaging, where the message travels through the internet instead of over your carrier's SMS network.Although most popular apps (such WhatsApp and Facebook Messenger) provide end-to-end encryption, we recommend using Signal because of the amount of metadata it collects. Metadata is all the information about the message besides their content. Who the message went to, the location of each user and even the IP address of those communicating are just some examples of metadata collected by companies. Signal collects the least amount of metadata compared to its competitors.Install Signal Private Messenger for free from the Play Store Don't Miss: How to Password-Protect Your Calls and Texts Using SignalSignal only collects your phone number, randomly generated authentication tokens, and profile information, such as an avatar and nothing more. Not only does it protect your messages from being compromised, but if Signal became compromised, hackers would gain insufficient information about you.Signal also offers secure calling using VoIP. Similar to text messages, voice calls are weakly encrypted, and better protection is available using the internet. VoIP (Voice over Internet Protocol) is a system for voice calling over the web. Since Signal uses VoIP, end-to-end encryption is available to voice calls as well.As long as you and the people you communicate with use Signal, all your messages and phone calls will be encrypted throughout the entirety of their travels, greatly reducing the chances of an external party hacking the conversation. Signal also offers encrypted video calls to help keep all communications secure. If you want to learn more about how to use Signal Private Messenger, click on the link below to see all of our basic coverage on the topic.Don't Miss: Signal 101 Tutorials to Help You Get Started with Encrypted Messaging
Step 3: Secure Your EmailA frequent target for hackers is your email. Popular email clients such as Yahoo and Gmail have measures in place to keep your contents safe, but their priority is maintaining fast performance and ease of use. Therefore, they don't utilize the highest level of security to protect your emails. Recently, both Yahoo and Gmail had data breaches, with the former having the largest in history.With emails containing so much information about us (including bank statements, love letters, receipts, etc.), any unauthorized individual who gains access can learn significant information about you, which can be used for malicious purposes. However, like our messages, we don't have to continue to send unprotected emails.Similar to other forms of communication, your data is the most exposed while traveling between the sender and the recipient. For the highest level of protection, you want end-to-end encryption to secure your email from when you construct the message to when the recipient reads it. You also want the highest level of encryption that will evolve as hackers learn ways into current systems. Because of these reasons, we recommend using ProtonMail.Install ProtonMail for free from the Play Store ProtonMail is a modern looking email client which provides security in a few ways. First of all, it uses end-to-end encryption to protect your email throughout the entirety of its travel. However, unlike Gmail, your private key isn't accessible to ProtonMail, as it isn't uploaded to their servers, ensuring security from breaches.ProtonMail uses an open source cryptography which allows anyone to access their code. With it being open source, it will have faster adjustment to new exploits discovered. It also protects against intentionally made backdoors (security holes that enable continuous access that are unknown to the masses) since the public can see the entire code and become aware.Don't Miss: How to Send Encrypted Emails to Non-ProtonMail RecipientsProtonMail also records minimal metadata, none of which is personally identifiable information. Therefore, you are protected if a breach happens to ProtonMail or if someone wants to know whom you email. There is even an option for Self-Destructing Email which places a timer on emails you send, deleting them from the recipient's inbox once the timer expires. If you wish to learn more about ProtonMail, follow the link below for tutorials that were written with beginners in mind.Don't Miss: ProtonMail 101 Guides That Will Walk You Through Encrypted Email
Step 4: Take Care of the Little ThingsEven more important than the technology we use to communicate is the personal mistakes we make when it comes to security. These errors include what information we send in communication — particularly passwords. Even if the conversation is encrypted, you should never send passwords or other personally identifiable information in an email or text message. Most companies will never ask for this information through insecure lines of communication (especially email), so you should assume fraudulent activities if asked.Secondly, avoid using public Wi-Fi. These are havens used by hackers to access individuals' information, since it attracts many devices which typically employ minimal security measures. If you must use public Wi-Fi, a VPN will provide you essential security and privacy for any form of communication. However, it is good practice to avoid these areas. Connecting to public Wi-Fi hotspots can leave you susceptible to attacks. Image by StockSnap/Pixabay Finally, discuss security with family and friends. Even if you use a secure line of communication, if the destination is insecure, your content is exposed. To maximize the protection provided by Signal and ProtonMail, you both need to use the service. Share this article with your loved ones so you can both enjoy secure communications between each other.Because of the popularity of smartphones, communications have become more accessible and more frequent. Unfortunately, much of this communication is unencrypted and available for even low-skill hackers to access. By implementing these recommendations, you can provide yourself the necessary protection so that the person you intend to communicate with is the only person who can access it. After reading this, what steps did you take to secure your communications? Did you use the apps we suggested, or did you discover another one? Let us know in the comments below.Don't Miss: Android Security 101 — How to Securely Browse the WebFollow Gadget Hacks on Facebook, Twitter, Google+, YouTube, and Instagram Follow WonderHowTo on Facebook, Twitter, Pinterest, and Google+
Cover image and screenshots by Jon Knight/Gadget Hacks
How To: Drag & Drop on Your iPhone in iOS 11 How To: Change Siri's Voice from Female to Male in iOS 7 on Your iPhone News: iOS 11.3 Bug Removes Screenshot Previews for Some iPhone Users How To: The 9 Most Annoying Changes in iOS 11 & How to Fix Them
Apple iOS 11.3 Update Introduces Brand New Set of Animoji
s ometimes, stock just doesn't cut it. When you're sick of the limitations in Sense on your HTC One, a new ROM can be a ray of sunshine. By installing a custom ROM, you can add or unlock new features in Sense, or you can get a pure Android experience instead.
How to Install a Custom ROM on your HTC One M8 - YouTube
How To: Instantly Unlock Your iPhone with Face ID — No Swipe Needed News: Essential iPhone X Tips for the 6 Million Lucky People Who Got One on Black Friday How To: Show Someone a Photo on Your iPhone Without Them Swiping Through All of Your Pics How To: Activate Siri on Your iPhone X S, X S Max, or X R
Show a Photo On Your iPhone Without Someone Accessing Camera Roll
osxdaily.com/2014/08/15/show-photo-iphone-without-camera-roll-access/
Have you ever wanted to share an iPhone picture with someone, but you're concerned about them flipping through your camera roll and finding other photos you'd rather not share? If you want to limit that you have a few options available, but because the iPhone doesn't have a specific ability to
How to Stop Nosy Friends from Viewing More Photos on Android
The parabolic microphone works by reflecting sound waves from a larger area (the reflector dish) into a smaller area (the microphone). In order to make your parabolic microphone work, you need to find this focal point. The simplest method is to place the microphone in the center of the dish.
Making and Testing a Homemade Parabolic Mic - YouTube
Microsoft has made Windows 10 the most cloud-oriented Windows version so far, as it has provided its user with some handy features. Some of these features in general shares your personal data to the Microsoft servers which means that they can snoop whatever you have been doing regarding some features.
How To: Everything You Need to Disable in Windows 10
The new Siri app allows you to use voice commands to search, use apps, and more. The app is available as a beta version in the iOS 5 release for the iPhone 4 S.This guide will show you how to use different voice commands to control Siri.
Use Siri on all your Apple devices - Apple Support
My video will tell you how to manage the start menu and the Live Tile functions. This includes adding and removing tiles, organizing them into groups and turning off the Live features. In addition, it is also possible to completely remove the Live Tile area so that it functions more like the traditional start menu from Windows 7.
How To Resize, Group & Manage App Tiles In Windows 8 Start Screen
Here is how to unlock Samsung Galaxy S4 without losing data. Step 1. Download, install and start the program on your computer. Then you need to click on the "Unlock" option from the main interface of the software to proceed.
How to Get the Android L Lock Screen on Your Galaxy S4 or
How to Change Your Name on Facebook. This wikiHow teaches you how to change your displayed name on Facebook, both in the mobile app and on the desktop site. Exercise caution when doing this, since Facebook will only allow you to change
During the Google I/O 2019 keynote, the latest Android Q Beta was released to the public for Pixel smartphones along with 15 other non-Pixel devices. It's the third Developer Preview for Android 10, but it's the first official public beta outside of Google's Pixel smartphones. A new public beta
The Pixel 3a XL Is Shaping Up to Be the Best Google Phone
Turn Your Android Tablet Into a Car Head Unit: I recently finished integrating a docking system in my 2005 Subaru Baja for my Asus Nexus 7 (2013). Here's a write-up about my project with some pictures and a parts list for anyone looking to do something similar.A standard car radio is fine, but
United States President Barack Obama will today sign a bill that makes cell phone unlocking legal again, writing the Unlocking Consumer Choice and Wireless Competition Act into law following its
President signs cell phone unlocking bill into law - CNET
0 comments:
Post a Comment